Array
(
[1536x1536] => Array
(
[width] => 1536
[height] => 1536
[crop] =>
)
[2048x2048] => Array
(
[width] => 2048
[height] => 2048
[crop] =>
)
[rta_thumb_no_cropped_420x] => Array
(
[width] => 420
[height] => 0
[crop] =>
)
[et-pb-gallery-module-image-portrait] => Array
(
[width] => 400
[height] => 300
[crop] => 1
)
[et-pb-post-main-image-fullwidth-large] => Array
(
[width] => 0
[height] => 0
[crop] => 1
)
[et-pb-image--responsive--desktop] => Array
(
[width] => 1280
[height] => 720
[crop] => 1
)
[et-pb-image--responsive--tablet] => Array
(
[width] => 980
[height] => 551
[crop] => 1
)
[et-pb-image--responsive--phone] => Array
(
[width] => 480
[height] => 270
[crop] => 1
)
)

Daylight Savings Time will end this year on Sunday, November 2, 2014. Aside from the extra hour of sleep and the evening commute in darkness little will change for the business world. Almost all technological devices – from the smartphone whose alarm you depend on to...
Discover More
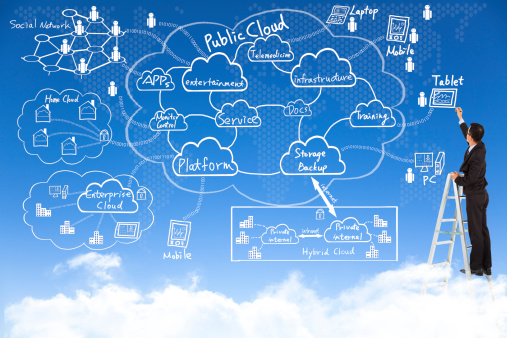
The productivity suite is the beating heart of the day-to-day activities of many businesses. A person’s work is only as good as their tools allow them to be, and the competition between Microsoft and Google to offer the best toolbox is to the benefit of users on both...
Discover More

Finally – IT Support That’s Responsive, Knowledgeable & Timely! When technology issues occur, there’s no time to waste because wasted time equals wasted money. CTECH Consulting Group understands how valuable your time is. Our helpdesk service professionals are everything...
Discover More

Protect Your Technology Against the Inevitable Threats of the Future! How does CTECH Consulting Group’s team of IT security experts keep you safe and secure against any threat the future holds? Here’s a few ways: Email Security We’ll analyze your email to search for any weak...
Discover More

Make Your Workforce MORE Mobile Than Ever Before! We believe your IT should help you get work done faster, more efficiently, in more places. A modern business lives and breathes outside of the office; so go ahead, start embracing the new way of using information...
Discover More
Page 1 of 612345...»Last »






